Welcome to this latest CTO Insights November newsletter, it has been a hectic time recently so please excuse the extended gap between editions. I’m sure you are keen to know what’s been catching my attention since we last spoke?
Something new
As a CTO I’m always looking for new crazy ideas to share information, and here’s one of them, our new CTO Insights videos! This series of videos sees me chat with an industry expert about a particular topic. First is Jon Hope, Senior Technologist at Sophos. Jon joined me for a wide ranging chat about the current state of cyber security and what the future holds.
The overall chat is around 30 minutes, but to make life a little easier I’ve broken it down into bite size 5 minute videos.
The first two of these (alongside the longer version) are available for you now.
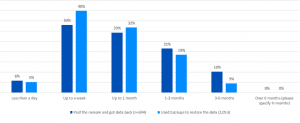
In part one we discuss the recently released Sophos Ransomware Threat report and what it means for CTO/CISOs and whether paying ransoms is ever the right thing to do.
You’ll find part one here.
In part two, we discuss the inevitability of attacks, how attacks have modified into double and triple “dip” attacks and what to do about them. We also discuss incident response plans and why it’s essential to have them.
I’d love your feedback on the format and what topics you’d like me to cover in future videos.
Looking after your security team
Back in mid-September I attended a Future of Cybersecurity event in Manchester. There was the usual mix of vendors and presentations. But two in particularly caught my attention as they discussed Cybersecurity wellbeing. The sessions shared a couple of troubling facts.
- Gartner reported 25% of Cyber Security Leaders will change careers by 2025 due to burnout.
- Forrester reported that of IT security staff 66% of them felt they were suffering stress and of those a further 50% were taking medication to help.
Those statistics are not things we can accept, and we cannot shrug our shoulders and hope it gets better. Even from the most basic of business views, it is untenable as over stressed staff are more likely to make mistakes and when it comes to cybersecurity it is mistakes that threat actors prey on.
How do we remove stress from our team? I imagine there is no easy answer and I’m not going to try to give one, but I did find a couple of good tips in this Watchguard Blog.
End user education – Education can help reduce threats and incidents and therefore the burden on your security teams.
Automation – Automate repetitive and time-consuming tasks so the team can stay focused on the priority areas.
Consolidation – Reducing the amount of technology vendors in your security suite, this can help both reduce risks caused by gaps between tools and also improve operations by allowing more to be achieved within a single platform.
There’s a couple of other additions I’d consider.
Managed Services and AI – Managed solutions such as MDR can help greatly reduce the burden on security teams, providing them with experienced security team on hand 24×7. It’s also worth looking at how vendors are using AI to reduce time consuming tasks and help prioritise risk and threats.
Security Culture – Build as positive a security culture as you can, make sure both your staff and your security teams feel that they are taken seriously, listened too and supported and if the worst happens, there will be no scapegoating. Security is too complex to expect perfection, so let’s not apply pressure by thinking that it is.
Your Copilot to the future

Back in October I attended Microsoft’s Envision conference in London. Which brought out the Microsoft “big guns” none bigger than CEO Satya Nadella (Seen here with UK CEO Clare Barclay). The event was focused on Microsoft’s Copilot technology. Copilot is the product name for its integration of generative AI throughout its Cloud Platforms. This ranges from the generally accessible Bing Chat service, which provides you with GPT 4 powered integration with its search engine, through to its subscription add on services like integrating data sets for building learning model and its soon to be available Security Copilot.
Copilot is interesting, as it is likley to be the first fully enterprise managed, large scale AI that many businesses will see. It will be baked into everyday tasks, from content creation to summarising long documents and Teams meetings. It is this, in a common everyday application like Microsoft 365, which is likley to bring business AI to the masses. I’m fascinated to see how this will be adopted and were it will lead to both innovation and better understanding of risks. We recently did a Tech Takeaways Episode – Exploring the Horizon with Microsoft Copilot discussing a little more about Copilot and its potential impact.
I’d be interested to hear from others about your thoughts and plans for Copilot, so do please share them.
That’s all for this edition of the newsletter, I have a couple of week’s of travel coming up, with a little holiday in Denmark before setting off to London for BlackHat Europe, so if you are going to be at the event, let me know.
Look out for the next CTO Insight Newsletter coming soon.




 One thing that people in IT don’t consider often enough, in my opinion, is the importance of engaging with an organisation. Asking questions to help better understand what the organisation needs from its IT team, in order to function better and be more successful. Too often we find ourselves, delivering IT solutions that were not asked for and we are then surprised when we get “push-back” to its adoption. It is important to remember that IT is there to empower and enable an organisation, rather than to launch “cool” IT solutions upon it.
One thing that people in IT don’t consider often enough, in my opinion, is the importance of engaging with an organisation. Asking questions to help better understand what the organisation needs from its IT team, in order to function better and be more successful. Too often we find ourselves, delivering IT solutions that were not asked for and we are then surprised when we get “push-back” to its adoption. It is important to remember that IT is there to empower and enable an organisation, rather than to launch “cool” IT solutions upon it. 




 Many of you would have met Paul during his time at Gardner’s. But for those that haven’t here’s a little about our new CTO. Paul studied Computing at Liverpool John Moore’s University. He got his first IT role at a pharmaceutical company in Liverpool, where he first met the Gardner Systems Team. He joined Gardner’s not long after and has worked across the business, from technical support to systems architect and today as CTO.
Many of you would have met Paul during his time at Gardner’s. But for those that haven’t here’s a little about our new CTO. Paul studied Computing at Liverpool John Moore’s University. He got his first IT role at a pharmaceutical company in Liverpool, where he first met the Gardner Systems Team. He joined Gardner’s not long after and has worked across the business, from technical support to systems architect and today as CTO.